Industrial Internet of Things (IIoT) Cybersecurity – Defending the Internet of Targets
Organizations are becoming increasingly reliant on adopting Industrial Internet of Things (IIoT) technologies that allow them to ramp up productivity and make smarter business decisions.
While enterprises stand to reap significant benefits from connected environments, IIoT adopters are uniquely susceptible to cyberattacks based on a few key factors. For one, more connected endpoints mean more opportunities for cybercriminals to gain entry into industrial systems.
There’s also the issue of operational equipment being adapted toward use cases they were never designed for, vulnerable communications protocols, and software-hardware configurations that vary considerably between organizations and industries.
In this article, we’ll discuss the biggest IIoT cybersecurity considerations organizations must be aware of before adopting new technologies and the risks they bring with them.
Safely Embracing the Industrial Internet of Things
Eager to tap new revenue streams hiding in unstructured data, businesses across a range of sectors are implementing IoT devices into their existing systems. However, every time a new device is integrated into the system, the threat surface expands, opening up new entry points attackers can exploit.
According to a report from Palo Alto Networks, 98% of IoT traffic is unencrypted, and nearly 60% of devices are vulnerable to moderate to severe cyber attacks.
Here are some of the key considerations involved in establishing a successful industrial internet of things cybersecurity plan.
Security Considerations for the IIoT Cybersecurity Challenge
- Potential Human Impacts. Because IT-OT convergence is a defining characteristic of IIoT systems, cybersecurity now extends into the physical world. Industrial IoT security requires organizations to consider how cyberattacks can result in public safety risks or things like grid outages that impact entire communities.
- Murky Regulatory Guidance. As it stands, there’s no official policy that defines how IoT data can be collected, accessed, and shared. As such, organizations are on their own and will need to develop a strategy that ensures adherence to personal privacy protection as well as industry-specific data management regulations.
- Data Management. Sensors can be embedded in just about anything, allowing organizations to collect information on a massive scale. Organizations will need to come up with a plan for securely managing sensitive information, and how they’ll efficiently process and store the torrent of data without causing latency issues.
- Interoperability Challenges. Industrial IoT ecosystems are typically composed of multiple devices, software, hardware, and legacy equipment that weren’t designed to work together. This leaves a lot of room for configuration errors, which could compromise the entire system.
Why Is Security Especially Important For Industrial IoT Systems?
IIoT cybersecurity is critical for organizations because the consequences of getting it wrong could have devastating real-world effects.
While any data breach or a ransomware attack can cause significant losses for a company, the impact is mainly financial or reputational. Companies may get fined. They’ll issue an apology and outline the steps they’ll take to protect customers better. When OT systems enter the picture, a cyber attack can introduce physical consequences, with effects that ripple throughout entire communities. Here are a few possibilities:
- Cyber terrorism. Attacks from terrorist groups or outside governments might sound far fetched, but they’re a real threat to the OT sector. These types of attacks are often carried out by sophisticated cybercriminals and are aimed at critical infrastructure.
- IP Leakage. Vulnerable IIoT systems could open the door to risks such as IP leakage, enabling the theft of trade secrets or sensitive data.
- Production Sabotage. In manufacturing facilities, vulnerable systems can introduce the threat of production sabotage. Attacks might target robots, putting workers at risk or an attacker might introduce defects in the production line by tampering with production logic. Attackers might also alter products, then ask for a ransom to prevent defective products from hitting consumer markets.
What Makes the IIoT Difficult to Secure?
The IIoT presents some unique security challenges, as the same characteristics that drive its transformative benefits are the source of its biggest threats. IIoT systems might be spread across several locations, each with hundreds or thousands of connected devices exchanging massive amounts of data,
Legacy OT Equipment & Software
As demand for operational data continues to rise, organizations are outfitting legacy machinery with IIoT sensors, without implementing proper security protections. Many of these machines operate using outdated software and old hardware components with known vulnerabilities.
The big challenge here is, companies patching isn’t always possible for these machines, while upgrades require pausing production cycles, causing long periods of downtime. Backdoors leftover from previous breaches often go unnoticed, leaving systems vulnerable to threats like WannaCry ransomware attacks.
Incorrect Authentication Practices
Poorly-configured session and user authentication allow attackers to steal credentials such as user names, passwords, and keys, as well as take control over user accounts to hack into other parts of the system. In a converged OT-IT system, attackers can leverage credentials from IT environments to target OT infrastructure.
Interoperability
IIoT systems are made up of a collection of sensors, software, equipment, and hardware, configured based on industry requirements and the company’s unique operational needs.
This presents two significant challenges–getting these disconnected systems to work together and securing all endpoints–after all, just one improperly configured connection can put the entire system at risk.
Many organizations use proprietary software, which can be difficult to patch, update, and monitor for threats, leaving the network vulnerable to attacks.
Vulnerable OT Communication Protocols
In order to capture valuable data, many enterprises have made OT technologies like sensors, controllers, and actuators part of the smart factory. But while protocols like Modbus and Profinet monitor, control, and connect physical processes within the production line, they weren’t designed to detect cyber threats or authenticate user credentials.
Attackers have become increasingly aware of the vulnerability of legacy protocols. They are using tactics targeting IoT devices like self-propagating worms and peer-to-peer C2 communications to disrupt critical processes.
Disconnect Between OT and IT
In many organizations, IT and operations teams operate as separate entities with little contact with one another. IT teams focus on managing data flow and assets like computers, printers, and network equipment, whereas OT manages industrial machines and physical processes.
The challenge is, without IT-OT convergence, cultural differences, data silos, and a whole new set of considerations for both groups can stand in the way of implementing and monitoring security controls.
We recommend that operations teams work closely with an IT pro experienced in IIoT adoption.
More Connectivity, More Risk
According to a 2019 Ponemon Institute report, 90% of organizations that use OT solutions fell victim to a cyberattack in the two years prior. What’s more, 20% of those surveyed believed that they had enough visibility into their attack surface to act on incoming threats.
For organizations considering adoption, it’s critical to understand that you’re going to be attacked sooner or later. To get ahead of this, organizations must map out the entire attack surface and perform a comprehensive evaluation to understand the level of risk.
From there, you’ll come up with a plan to transfer, reduce, and prevent each potential threat.
Look Toward OWASP Standards
For a better sense of which threats you’ll need to consider, we recommend looking toward the Open Web Application Security Project (OWASP) list of Top 10 Vulnerabilities.
OWASP is a non-profit group that offers unbiased cybersecurity information and guidance and compliance with the standards outlined below will help you address the vulnerabilities that are most likely to be exploited.
You can read the full report here but here’s a quick look at what to look out for:
- Weak, Easy-to-Guess Passwords.
- Insecure Network Services.
- Insecure Ecosystem Interfaces.
- Lack of Secure Update Mechanism.
- Use of Outdated or Insecure Components.
- Insufficient Privacy Protection.
- Insecure Data Transfer and Storage.
- Lack of Device Management.
- Insecure Default Settings.
- Lack of Physical Hardening.
Setting IIoT cybersecurity policies based on the OWASP list is a great place to start when it comes to reducing the threats to your system.
What Are Some Best Practices for Maintaining Industrial Ineternet of Things Security?
While there’s no official set of “rules” for ensuring that your industrial IoT system stays secured, we typically recommend that organizations work with IT experts to adapt the Center for Internet Security (CIS) 20 Critical Cybersecurity Controls to your IoT infrastructure.
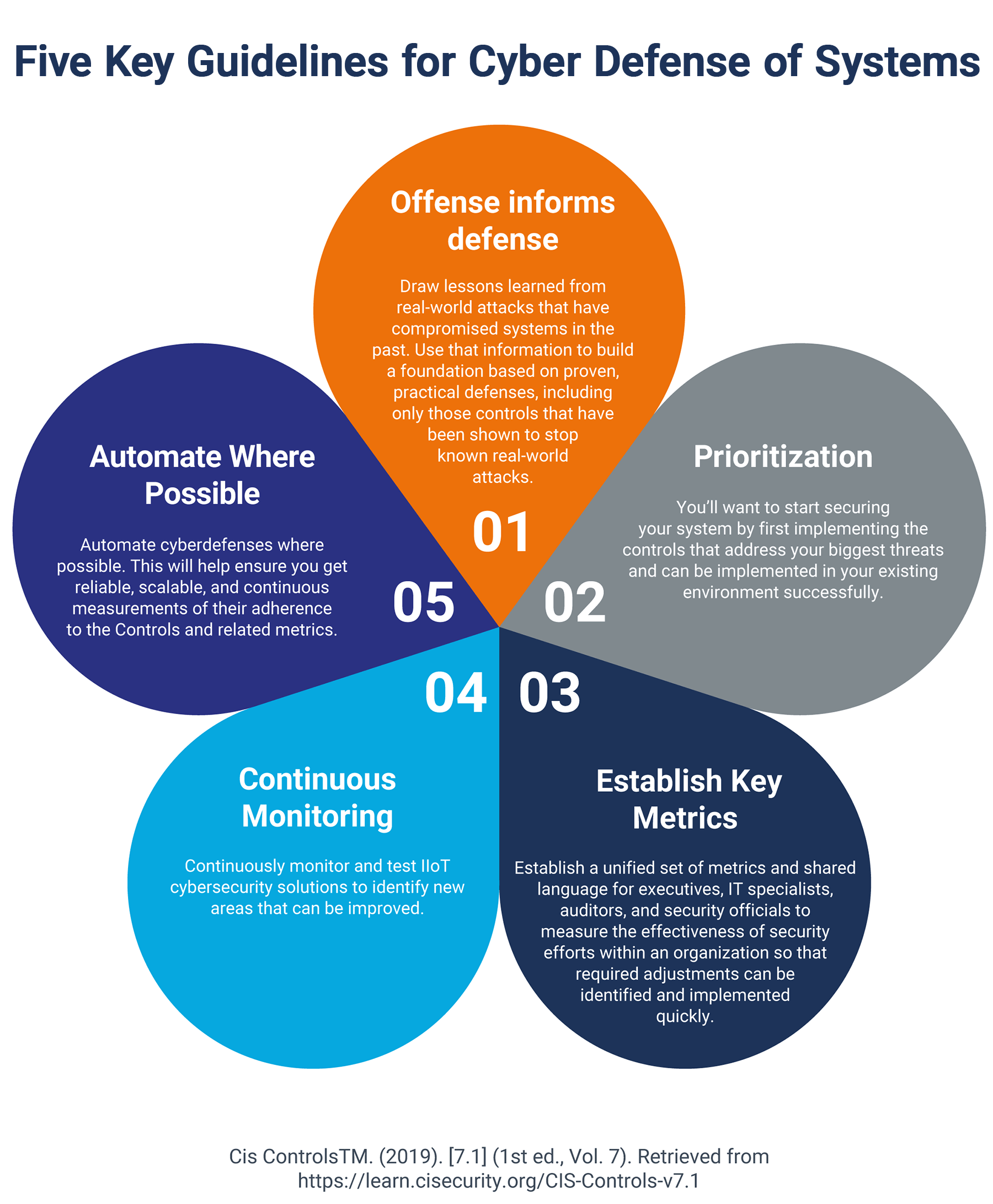
The CIS Controls center around five core principles, which are as follows:
- Offense informs defense. Draw lessons learned from real-world attacks that have compromised systems in the past. Use that information to build a foundation based on proven, practical defenses, including only those controls that have been shown to stop known real-world attacks.
- Prioritization. You’ll want to start securing your system by first implementing the controls that address your biggest threats and can be implemented in your existing environment successfully.
- Establish Key Metrics. Establish a unified set of metrics shared language for executives, IT specialists, auditors, and security officials to measure the effectiveness of security measures within an organization so that required adjustments can be identified and implemented quickly.
- Continuous Monitoring. Continuously monitor and test IIoT cybersecurity solutions to measure their effectiveness and identify new areas that can be improved.
- Automate Where Possible. Automate cyberdefenses where possible. This will help ensure that reliable, scalable, and continuous measurements of their adherence to the Controls and related metrics.
We recommend downloading the full report for a deep dive into all 20 controls, but here’s how CIS breaks them down, organizing them into three categories–basic, foundational, and organizational.
Basic
- Inventory & Control of Hardware Assets
- Inventory and Control of Software Assets
- Continuous Vulnerability Management
- Controlled Use of Admin Privileges
- Secure Configuration for all Hardware and Software Across All Devices
- Maintenance, Monitoring, and Analysis of Audit Logs
Foundational
- Establish Email and Browser Protections
- Set Up Malware Defenses
- Set Limits and Controls of Protocols, Ports, and Services
- Implement Data Recovery Solutions
- Secure Configuration for Network Devices
- Boundary Defense
- Data Protection
- Control Access on a Need to Know Basis
- Establish Wireless Access Control
- Account Monitoring and Control
Organizational
- Develop and Implement Security Awareness and Training Initiatives
- Application Software Security
- Incident Response and Management
- Penetration Testing & Red Team Exercises
Wrapping Up
As the IIoT continues to gain momentum, enterprises need to consider the security threats coming from all endpoints and take steps to protect themselves from harmful, potentially life-threatening cyberattacks.
[adinserter name=”IIoT Closing”]
Recent blog posts

Stay in Touch
Keep your competitive edge – subscribe to our newsletter for updates on emerging software engineering, data and AI, and cloud technology trends.